Outsourcing data security protocols
Data management and information security are important factors to explore when outsourcing to The Philippines. It’s important to note that not every outsourcing provider will have the same facilities, protocols and infrastructure. Here at Beepo, we take data security very seriously and have multiple levels of security in place to deliver peace of mind when sharing your data with your employees over in the Philippines.

Our data privacy and information security protocol
Given the continuous tightening of regulations surrounding data security, privacy and information management, Beepo has a nine-part, finance-industry-standard security protocol in its office located in Clark, The Philippines. Our parent company, Probe CX, also has a dedicated Cyber Security and Risk Manager who handles information security policies and procedures.
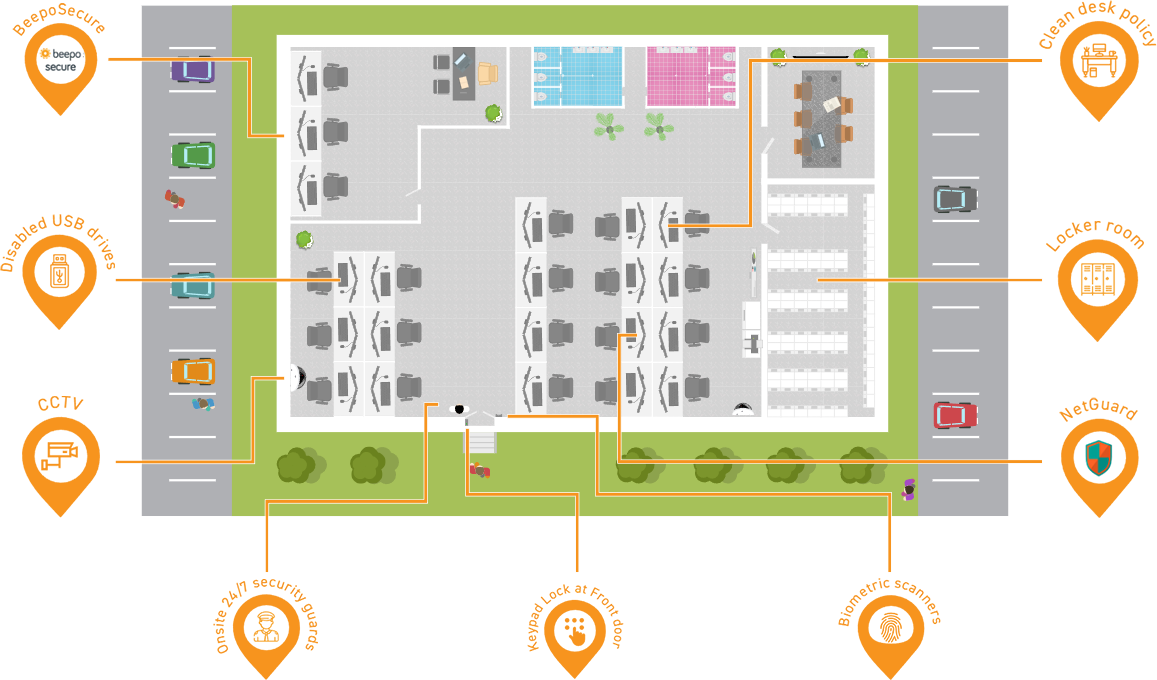
NOTE: This is not an exact representation of the Beepo floor space. It provides context as to how all nine security features work together to mitigate risk.
Security at Beepo starts at the front door. All employees need to use a code to enter the building. With keypad locks at all external entrances, only senior staff and security have access to the building outside of operating hours. This simple measure ensures all line staff only have access to the building when senior staff and supervisors are at work.
The main entrance and reception area are staffed by security guards 24/7. They only allow employees and approved visitors through reception and also perform spot searches. Spot searching ensures staff do not take any recording or electronic devices into the main operations area.
Each staff member at Beepo has their own locker. The locker room is located after reception and before the main operations area. Employees are required to place all personal recording devices in their lockers prior to entering the workspace.
Upon entering the main operations area, employees are required to be identified by scanning their fingerprints using biometric scanners. The biometric scanners ensure only staff have access to the operations area while visitors need to be authorised by management prior to gaining access.
It is a Philippine government requirement that all outsourcing companies have CCTV throughout. At Beepo, CCTV covers all reasonable spaces inside and outside the building, maintaining a thorough record of staff movements.
Our strict clean desk policy prevents staff from having anything on their desk that would allow them to record sensitive information. This policy is actively enforced by our client experience team.
All computers have disabled USB drives ensuring staff cannot use USBs or devices to download any client data.
Your outsourced team use BeepoSecure; which is a cloud-based product that allows single sign-on access to all software applications. It means you don’t have to provide usernames and passwords to your Beepo employees; instead, login details are uploaded directly to the BeepoSecure platform. This means Beepo staff cannot log in to your applications outside of the office and computers can even be locked down to prevent them from signing on outside of work hours.
Employee internet activity is managed and monitored through NetGuard; a cloud-based platform. NetGuard allows Beepo to lockdown internet access to only those websites and cloud-based applications your staff need to do their job.
Our IT data privacy tools
To add that extra level of information security, Beepo has a dedicated internal IT department that works hard to implement further online security processes to ensure a high level of data privacy is provided for all our clients (whether they are in-office or working remotely):
 Bitdefender: provides anti-virus software, cyber security, content control and anti-malware.
Bitdefender: provides anti-virus software, cyber security, content control and anti-malware.
 Regular system and security patches: applied to computers on a routine basis or as per Microsoft updates
Regular system and security patches: applied to computers on a routine basis or as per Microsoft updates
 Encrypted disks: Bitlocker encrypted disks to ensure that if a PC was stolen, no data can be accessed on the disk.
Encrypted disks: Bitlocker encrypted disks to ensure that if a PC was stolen, no data can be accessed on the disk.
 Secure disposal of IT equipment: both media and equipment is inspected for possible data breaches before deploying
Secure disposal of IT equipment: both media and equipment is inspected for possible data breaches before deploying
 Local administrator blocked: staff working from home (or in the office) do not have local administrator rights.
Local administrator blocked: staff working from home (or in the office) do not have local administrator rights.
 IDS & IPS secure: intrusion detection systems and intrusion prevention systems are used throughout the organisation.
IDS & IPS secure: intrusion detection systems and intrusion prevention systems are used throughout the organisation.
 Firewall: Watchguard firewall enabled on all Beepo devices.
Firewall: Watchguard firewall enabled on all Beepo devices.
Our human resources measures
As we source and recruit your outsourced team, there are a few key security measures that we take into consideration:
 Background checks: verify identity, academic qualifications and experience
Background checks: verify identity, academic qualifications and experience
 Security clearances: highlight criminal misconducts and key areas of security concern
Security clearances: highlight criminal misconducts and key areas of security concern
 Medical examinations: ensure employees are fit for work
Medical examinations: ensure employees are fit for work
 Employment contracts: emphasise data security best practices and failure to comply actions.
Employment contracts: emphasise data security best practices and failure to comply actions.

























.jpg?width=270&height=160&name=How%20to%20plan%20for%20the%20post-JobKeeper%20business%20environment%20(1).jpg)
















.jpg?width=299&height=196&name=Mega%20Menu_FAQs%20(1).jpg)

